Several compromised remote computers redirect incoming HTTP traffic on TCP port 80 to the central web server with the help of the redir port redirector.
正如我们观察到,并在本文所描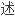
 ,
, 些时候多种方法将提供
些时候多种方法将提供 些冗余性,并通过
些冗余性,并通过 个两层
个两层
 络拓扑配置保护他们
络拓扑配置保护他们
 络钓鱼攻击基础设置。
络钓鱼攻击基础设置。
Several compromised remote computers redirect incoming HTTP traffic on TCP port 80 to the central web server with the help of the redir port redirector.
正如我们观察到,并在本文所描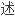
 ,
, 些时候多种方法将提供
些时候多种方法将提供 些冗余性,并通过
些冗余性,并通过 个两层
个两层
 络拓扑配置保护他们
络拓扑配置保护他们
 络钓鱼攻击基础设置。
络钓鱼攻击基础设置。
声明:以

 、词性分类均由互联
、词性分类均由互联 资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件
资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件 观点;若发现问题,欢迎向我们指正。
观点;若发现问题,欢迎向我们指正。